Enhancing Cloud Security: Best Practices for AWS Control Tower

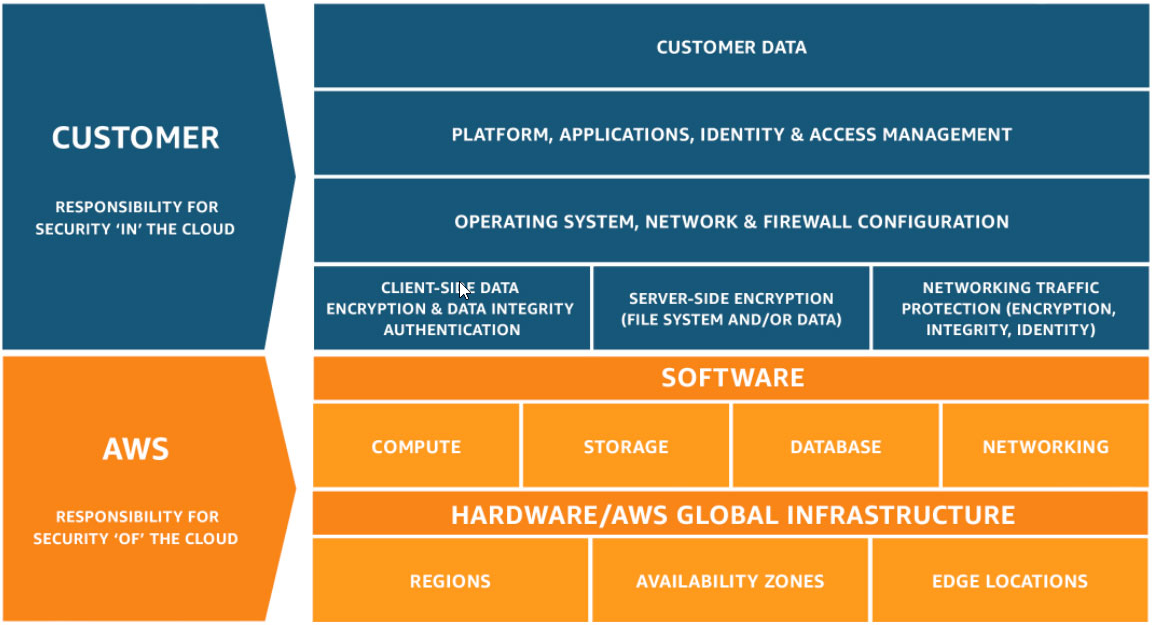
Cloud Security is job Zero at AWS, everyone needs to have a secure environment. AWS ensures that its customers benefit from a data center and network architecture that is designed to meet the security needs of even the most sensitive organizations. The responsibility for security in Control Tower is shared between AWS and its customers, as per the shared responsibility model, which includes two aspects.
Security of the cloud: AWS is responsible for protecting the infrastructure that runs AWS services in the AWS Cloud. AWS also provides secure services to customers. Independent auditors regularly test and verify the effectiveness of AWS security through compliance programs.
Security in the cloud: Customers are responsible for their use of AWS services, including factors like data sensitivity, organizational requirements, and compliance with laws and regulations.
This blog aims to educate you on applying the shared responsibility model while using AWS Control Tower.
Data Protection in AWS Control Tower
AWS Control Tower follows a shared responsibility model for data protection, where AWS takes charge of safeguarding the infrastructure that underpins the entire AWS Cloud, while you are responsible for overseeing the content you host on this infrastructure. This means that you need to manage and configure security measures for the AWS services you utilize.
To ensure the protection of your data, AWS suggests protecting your AWS account credentials and creating separate user accounts with either AWS IAM Identity Center (formerly known as AWS Single Sign-On) or AWS Identity and Access Management (IAM), which will only grant users the necessary permissions for their job responsibilities. Additionally, AWS recommends implementing the following security measures
- Enable multi-factor authentication (MFA) for every account.
- Use SSL/TLS to communicate with AWS resources.
- Set up API and user activity logging through AWS CloudTrail.
- Utilize AWS encryption solutions and all default security controls within AWS services.
- Take advantage of advanced managed security services, like
- Amazon Macie, to detect any sensitive data stored in Amazon S3
- Amazon GuardDuty, to continuously monitors AWS accounts and workloads, detecting and reporting malicious activity.
Encryption at Rest – AWS Control Tower uses encrypted Amazon S3 buckets and DynamoDB databases to support your landing zone. The encryption at rest is configured using Amazon S3-Managed Keys by default, but you also have the option to add KMS encryption keys for enhanced protection. In addition, you have the ability to enable encryption at rest for the supported services within your landing zone, ensuring enhanced data security. Check out my blog on AWS KMS Encryption for more information.
Encryption in Transit – AWS Control Tower supports encryption in transit with TLS and client-side encryption. Access is only available through a secure HTTPS endpoint, and encryption is enabled by default during setup.
Restrict Access to Content – To follow best practices, limiting access to the necessary set of users is recommended. AWS Control Tower enables you to achieve this by ensuring that your central cloud administrators and end users have the appropriate IAM permissions or are assigned to the relevant groups for IAM Identity Center users.
Identity and access management in AWS Control Tower
To carry out any tasks in your landing zone, such as provisioning accounts in Account Factory or creating new organizational units (OUs), you must verify that you are an approved AWS user through either AWS Identity and Access Management (IAM) or AWS IAM Identity Center (successor to AWS Single Sign-On).
Once your identity has been authenticated, IAM will regulate your access to AWS by granting you specific permissions for particular operations and resources. If you are an account administrator, you can utilize IAM to manage the access of other IAM users to the resources linked to your account.
An account administrator (or administrator) is a user with administrator privileges.
In AWS cloud, it’s important to remember that resources are connected to an account and access is controlled by permissions policies, A permissions policy describes who has access to what. Account administrators have the ability to connect policies to IAM identities, and some services (like Lambda and S3) even allow policies to be attached directly to resources. To ensure proper permissions management, it’s crucial to keep track of users/roles, resources, and necessary actions that must be allowed for operating those resources.
In AWS Control Tower, the primary resource is a landing zone. AWS Control Tower also supports an additional resource type, controls, sometimes called guardrails. However, for AWS Control Tower, you can manage controls only in the context of an existing landing zone. Controls can be referred to as a subresource.
Compliance Validation for AWS Control Tower
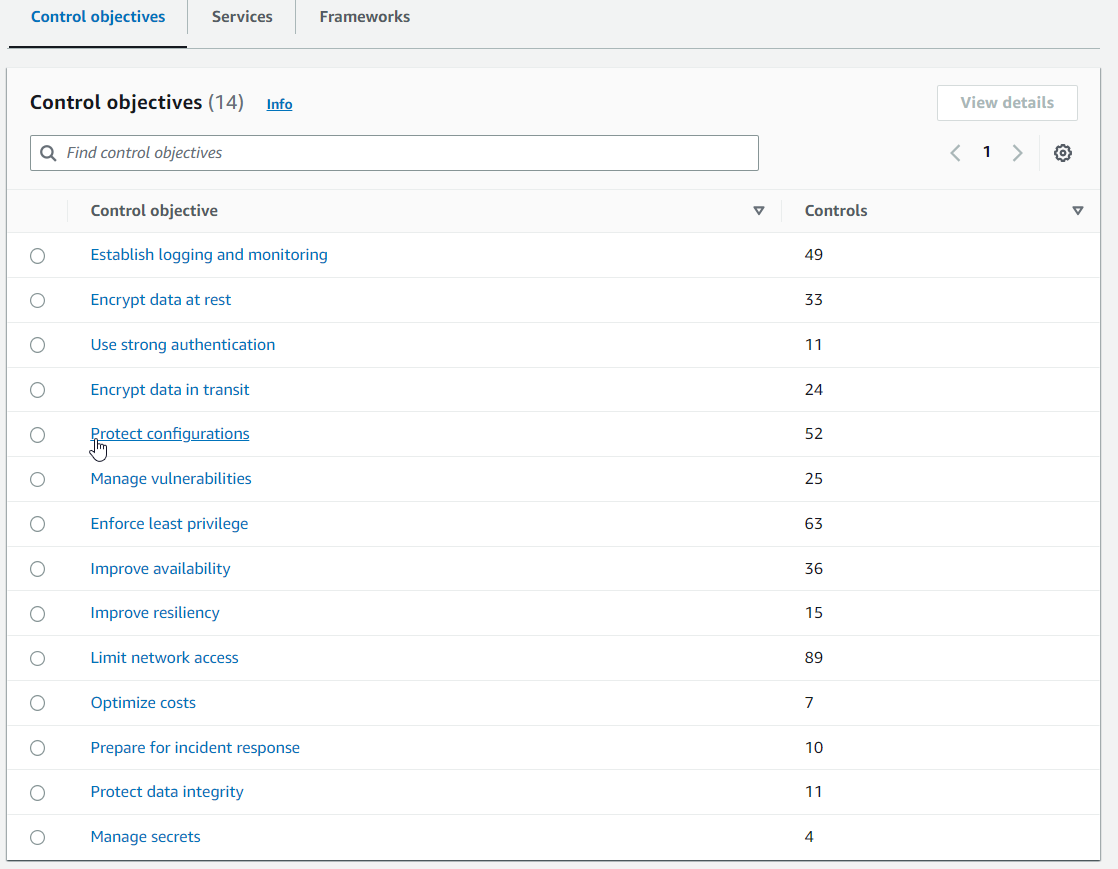
By using Control Tower, you can apply predefined controls that align with industry-standard compliance frameworks such as NIST, CIS AWS Benchmark, and PCI DSS. These controls are tailored to address specific security and compliance requirements outlined in these frameworks. This feature saves time and effort by offering control objectives mapping and integration with compliance frameworks.
Control Objectives – A control objective is a target to be achieved, by means of implementing controls and configurations in your AWS Control Tower environment. In other words, a control objective is a high-level, conceptual objective that usually requires a group of controls working together.
Frameworks are sets of controls that adhere to industry-specific compliance requirements. AWS services manage these controls. The controls in each framework are defined by AWS experts who adhere to the best practices procedures and guidelines for managing risk. They establish configurations that AWS Control Tower manages on your behalf.
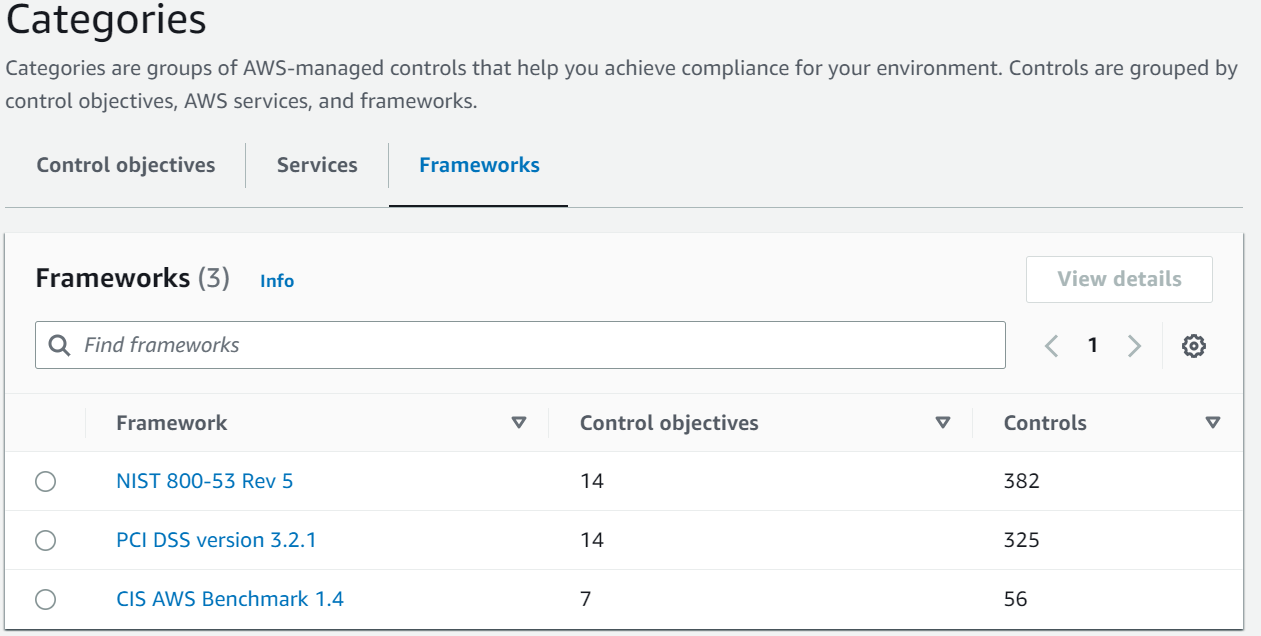
When utilizing AWS Control Tower, the responsibility for compliance falls on you, and is determined by several factors such as the sensitivity of data, compliance objectives of the company, and relevant laws and regulations. To aid in meeting these compliance requirements, AWS offers various resources. Link to the resources.
Resilience in Control Tower
When you set up your landing zone in Control Tower, it establishes a designated home region, which refers to the specific AWS Region where your landing zone is created. You cannot change your home region after setting up your Landing Zone. AWS, as a whole, operates on a global infrastructure framework centered around AWS Regions and Availability Zones.
AWS Regions are geographically dispersed and consist of multiple physically separated and isolated Availability Zones. These Availability Zones are connected by high-speed, low-latency, and redundant networking infrastructure. This architecture ensures that even in the event of localized failures or disruptions, the overall system remains resilient and accessible.
Infrastructure Security in AWS Control Tower
AWS Control Tower ensures the security of your environment by implementing AWS global network security measures. When accessing AWS services and resources within your landing zone, it is recommended to use AWS-published API calls over the network, with Transport Layer Security (TLS) 1.2 as a requirement and TLS 1.3 or newer being strongly recommended.
To authenticate API requests, you must sign them using an access key ID and secret access key associated with an IAM principal. Alternatively, you can utilize the AWS Security Token Service (AWS STS) to generate temporary security credentials for request signing.
You can set up security groups tailored to your AWS Control Tower landing zone workloads for enhanced network infrastructure security. For more details, refer to the Walkthrough: Set Up Security Groups in AWS Control Tower With AWS Firewall Manager.
Wrap Up!
In conclusion, security in AWS Control Tower follows a shared responsibility model. AWS is responsible for ensuring the safety of the underlying infrastructure, while customers are responsible for implementing security measures within their accounts and workloads. This includes data protection, access management through IAM, and compliance validation.
By understanding and fulfilling your role in this shared responsibility model allows you to create a secure AWS Control Tower environment and effectively protect your cloud resources.