Strengthening Security in AWS Control Tower through Centralized IAM Identity Center

In this blog, we’ll take a closer look into the Identity and Access Management aspect of AWS Control Tower’s managed environment. By default, AWS Control Tower uses AWS IAM Identity Center to set up and control access to AWS accounts that are created through the Account Factory unless you specifically opt for self-management of your identity and access control.
What is AWS IAM Identity Center?
Key features of AWS IAM Identity Center include
- Centralized User Management: AWS IAM Identity Center provides a central directory to manage user identities and access across multiple AWS accounts and applications.
- Single Sign-On (SSO) Experience: Users can sign in once and access all authorized AWS accounts and applications without needing separate credentials for each service.
- Integration with SAML 2.0: AWS IAM Identity Center supports Security Assertion Markup Language 2.0 (SAML 2.0), enabling integration with many popular identity providers (IdPs) and applications that support SAML-based SSO.
- Built-in Provisioning: AWS IAM Identity Center can synchronize user identities from an existing identity source, like Microsoft Active Directory, to AWS accounts, streamlining user onboarding and access management.
- Multi-factor Authentication (MFA): It supports MFA, adding an extra layer of security to user sign-ins.
- Permissions Management: Administrators can create and manage permissions for user groups, making granting access to resources easier.
- Audit and Monitoring: AWS IAM Identity Center provides audit logs and reporting capabilities to monitor user activity and access to AWS accounts and applications.
Setting up AWS Control Tower with IAM Identity Center
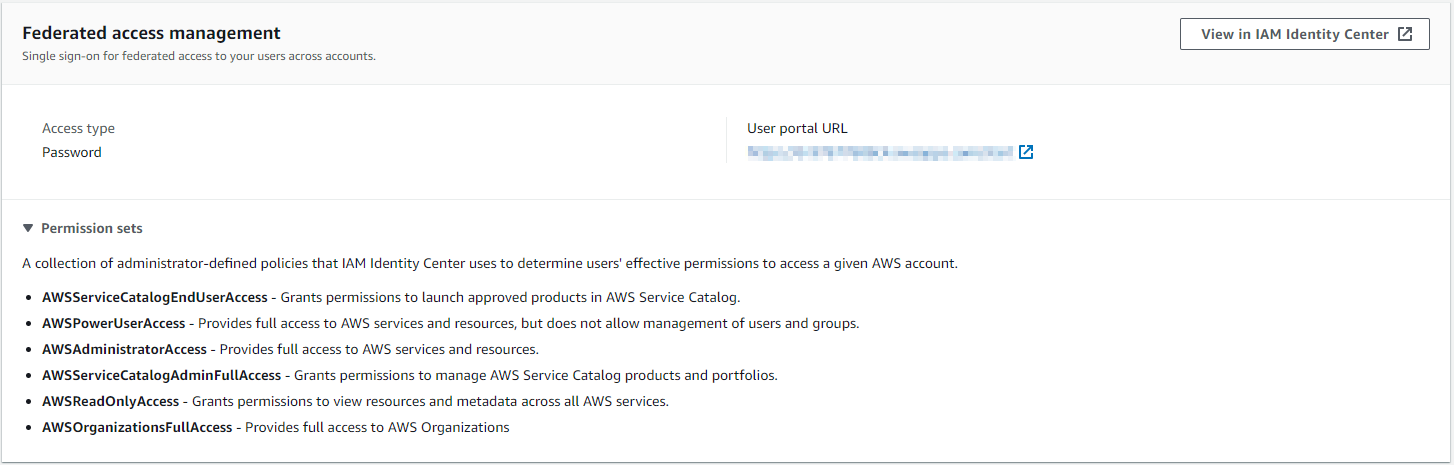
Federated Access Management
The IAM Identity Center allows for identity federation through the use of SAML (Security Assertion Markup Language) 2.0, an industry-standard protocol for securely exchanging information about a user between an identity provider (IdP) and a service provider (SP). This allows for federated single sign-on access for authorized users of applications within the AWS access portal.
A permission set is like a template you create and manage, defining a set of IAM policies. These permission sets make it easy to assign access to AWS accounts for users and groups in your organization. The IAM Identity Center utilizes permission sets to grant access to users or groups across multiple AWS accounts. By assigning a permission set, the IAM Identity Center will generate IAM roles that are managed by the IAM Identity Center and apply the policies outlined in the permission set to those roles. Authorized users can access these roles through the IAM Identity Center User Portal or AWS CLI.
AWS Control Tower setup comes with few predefined permission sets. In addition, you can create custom permission sets based on the business use case.
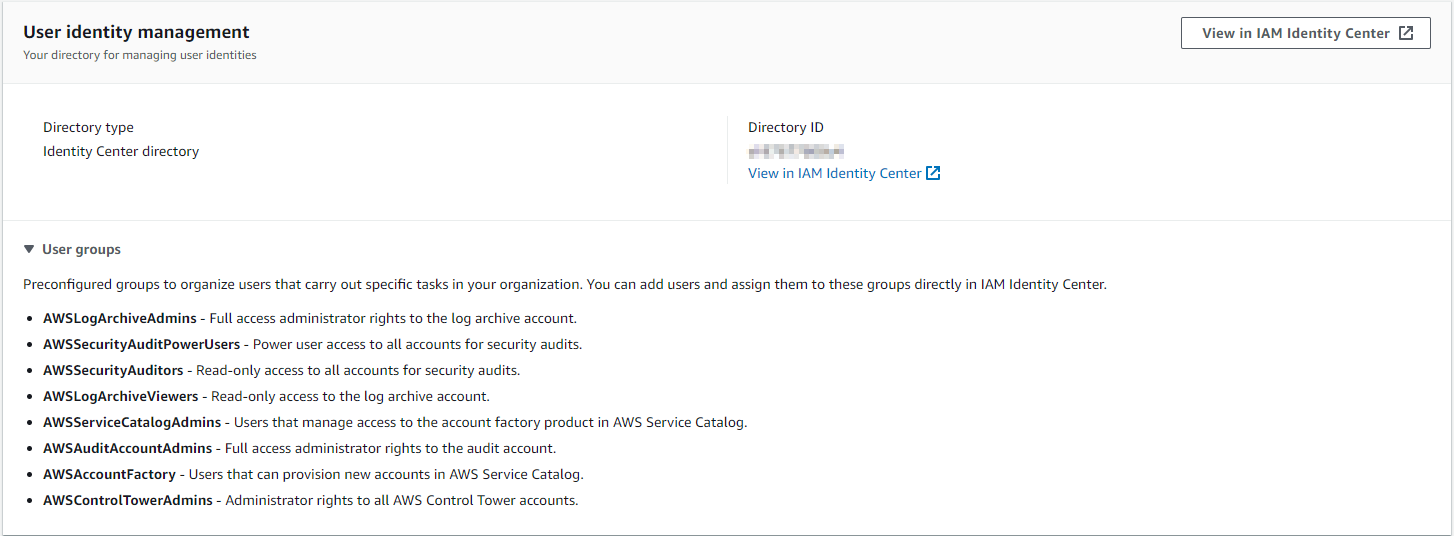
User identity Management
AWS Control Tower provides pre-configured User groups designed to organize users based on the specific tasks they perform in your accounts. You can easily add users and assign them to these groups directly in IAM Identity Center. This action aligns permission sets with the users in the respective groups within your accounts. When you set up your landing zone, the following groups are automatically created.
Permissions for configuring and provisioning accounts in Control Tower
With the AWS Control Tower Account Factory, AWS IAM Identity Center users (formerly known as AWS Single Sign-On) and cloud administrators can easily set up accounts in your landing zone. To provision accounts, users must belong to the AWSAccountFactory or management group. The AWS Control Tower management account has a trusted relationship with the AWSControlTowerExecution role, which enables account setup and some automated account setup.
The presence of the AWSControlTowerExecution role is essential in all enrolled accounts to facilitate AWS Control Tower’s management of individual accounts and reporting of relevant information to your designated Audit and Log Archive accounts.
You can add AWSControlTowerExecution role to an account, in different ways:
- For accounts in the Security OU (also known as core accounts), the role is automatically created during the initial setup of the AWS Control Tower.
- When creating an Account Factory account through the AWS Control Tower console, the AWSControlTowerExecution role is generated during account creation.
- For enrolling a single account, customers are required to manually create the AWSControlTowerExecution role and then proceed to register the account in AWS Control Tower.
When extending governance to an Organizational Unit (OU), AWS Control Tower uses the StackSet-AWSControlTowerExecutionRole to create the role in all accounts within that OU.
The AWSControlTowerExecution role serves the following purposes:
- It enables the automatic creation and enrollment of accounts through scripts and Lambda functions.
- It aids in configuring logging across your organization, ensuring that logs from all accounts are sent to the specified logging account.
- It facilitates the enrollment of individual accounts into AWS Control Tower for centralized management.
Considerations for AWS IAM Identity Center
If you have already established the AWS IAM Identity Center (previously known as AWS Single Sign-On), the AWS Control Tower home Region must match the IAM Identity Center Region. Furthermore, the installation of the IAM Identity Center is only possible in the management account of your organization. Lastly, depending on the identity source you select for your IAM Identity Center directory, there are three available options.
- IAM Identity Center User Store: When AWS Control Tower is set up with IAM Identity Center, it creates groups in the IAM Identity Center directory and grants access to these groups for the user you select in member accounts.
- Active Directory: If you set up IAM Identity Center for AWS Control Tower with Active Directory, AWS Control Tower does not manage the IAM Identity Center directory. It won’t assign users or groups to new AWS accounts.
- External Identity Provider: If you configure IAM Identity Center for AWS Control Tower with an external identity provider (IdP), AWS Control Tower generates groups in the IAM Identity Center directory and provides access to these groups for the user you choose in member accounts. During account creation in Account Factory, you can specify an existing user from your external IdP. AWS Control Tower will grant this user access to the newly created account when it synchronizes users with the same name between IAM Identity Center and the external IdP. Additionally, you can create groups in your external IdP that match the names of the default groups in AWS Control Tower. When you assign users to these groups, they can access your enrolled accounts.
Access to the Accounts
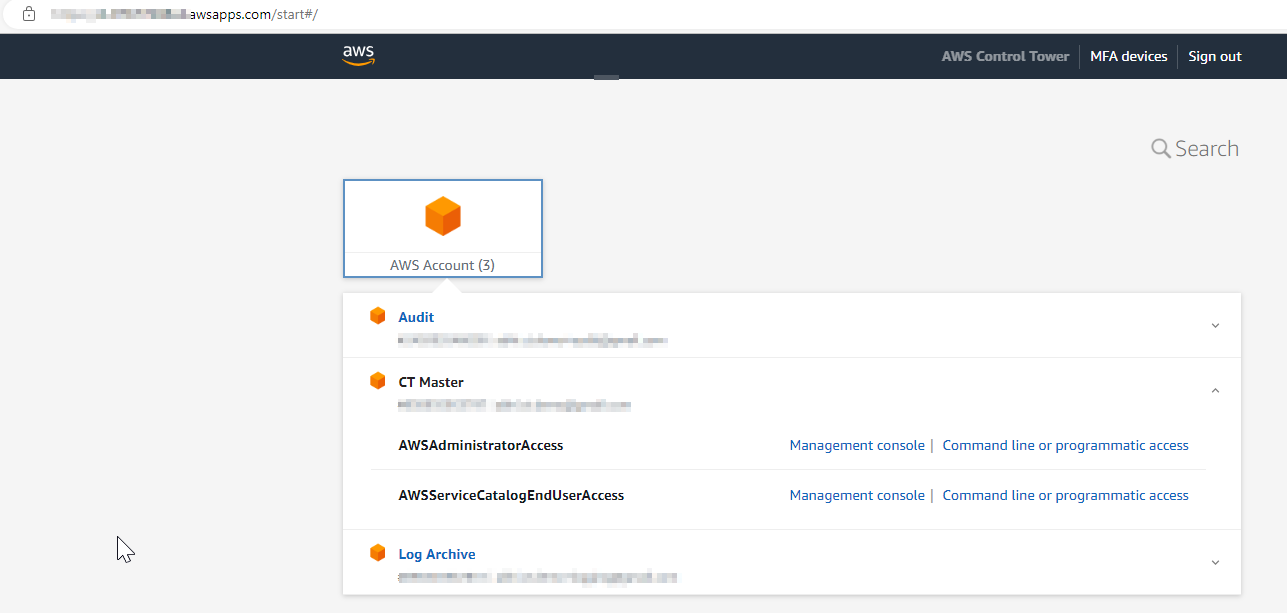
After setting up AWS Control Tower with IAM Identity Center, you can access your accounts in two ways: either through the Federated User portal URL or via AWS CLI.
Here is the console representation of Single-Sign-On page.
To get programmatic access to AWS IAM Identity Center managed account , you need to configure your profile with the aws configure sso wizard.
$ aws configure sso
SSO session name (Recommended): my-sso
SSO start URL [None]: https://my-sso-portal.awsapps.com/start
SSO region [None]: us-east-1
SSO registration scopes [None]: sso:account:access
Once you have configured the profile successfully, you can login to the console programmatically using aws sso login command.
aws sso login
Wrap Up!
In conclusion, AWS IAM Identity Center is a secure web-based service designed to streamline access management to various AWS services. It offers centralized control over AWS accounts and business applications, enabling efficient management of users and their security credentials. With IAM Identity Center, you gain the ability to control access and user permissions across all AWS accounts within AWS Control Tower.
One of the key benefits of IAM Identity Center is its support for authentication from external identity providers using SAML 2.0, simplifying the authentication process and enhancing the overall user experience within the AWS environment. This centralized and integrated approach to identity and access management benefit organizations to strengthen security, improve governance, and optimize workflows in their AWS infrastructure.