
What is AWS Control Tower?
The AWS Control Tower is a self-service tool that allows you the easiest way to Setup and Govern a multi-account AWS environment based on best practices. Helpful to both administrators and developers, it establishes a landing zone that is based on best-practices blueprints, and it enables governance using guardrails you can choose from a pre-packaged list of policies.
The Landing Zone is a well-architected, multi-account baseline that follows AWS best practices. AWS Landing Zone deploys an AWS Account Vending Machine (AVM) product for provisioning and automatically configuring new AWS accounts. This environment is customizable to allow customers to implement their account baselines through a Landing Zone configuration and update pipeline.
Guardrails are managed automated sets of policies that implement AWS best practices and meet regulatory compliance requirements. Guardrails have evolved dramatically, extending the principles of least privilege, separation of duties, and segmentation. They’re far more powerful when linked together in an AWS Control Tower, a single interface that enables secure operational and administrative functions while automatically enforcing governance policies throughout your organization.
Why do you need AWS Control Tower?
If you have multiple AWS accounts and teams in your organization, Cloud setup and governance can be a complex and time-consuming process; it slows down the innovation work you are trying to do. AWS Control Tower allows you to experiment, iterate, and migrate workloads without worrying about scalability or security concerns as your cloud footprint grows.
With Control Tower, you can
- Set up a multi-account well-architected AWS environment in a few clicks.
- Standardize account provisioning utilizing the Account factory (also known as Account Vending Machine) feature.
- Proactively enforce governance and compliance policies with Preventive and detective guardrails.
- Apply Identity and Access Management (IAM) using AWS SSO. IAM using AWS SSO provides a single point of identity to help you securely sign in to the AWS ecosystem.
- Gain continuous visibility into your multi account environment with the AWS Control Tower dashboard.
And a lot more.
AWS Landing Zone Base Setup
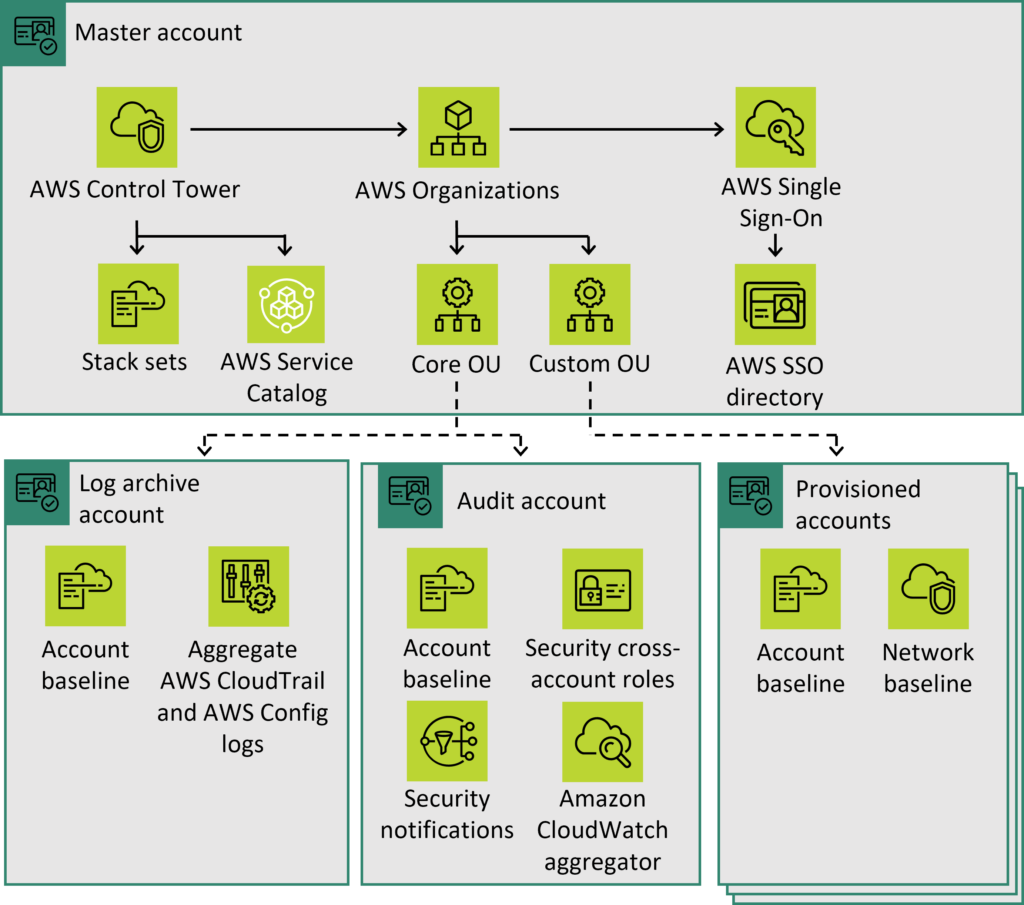
When you set up a landing zone, AWS Control Tower performs the following actions in your management account on your behalf:
- Creates two AWS Organizations organizational units (OUs): Security, and Sandbox (optional), contained within the organizational root structure.
- Creates two shared accounts in the Security OU: the Log Archive account and the Audit account.
- Enables centralized log archive using AWS Cloudtrail and AWS Config.
- Creates a cloud-native directory in AWS SSO, with preconfigured groups and single sign-on access.
- Cross-account audit access using AWS SSO and AWS IAM service.
- Applies twenty mandatory preventive guardrails to enforce policies.
- Applies two mandatory detective guardrails to detect configuration violations.
- Excluding the management account, guardrails applied to the organization as a whole.
- Enable end-user account provisioning through AWS Service Catalog product and portfolios.
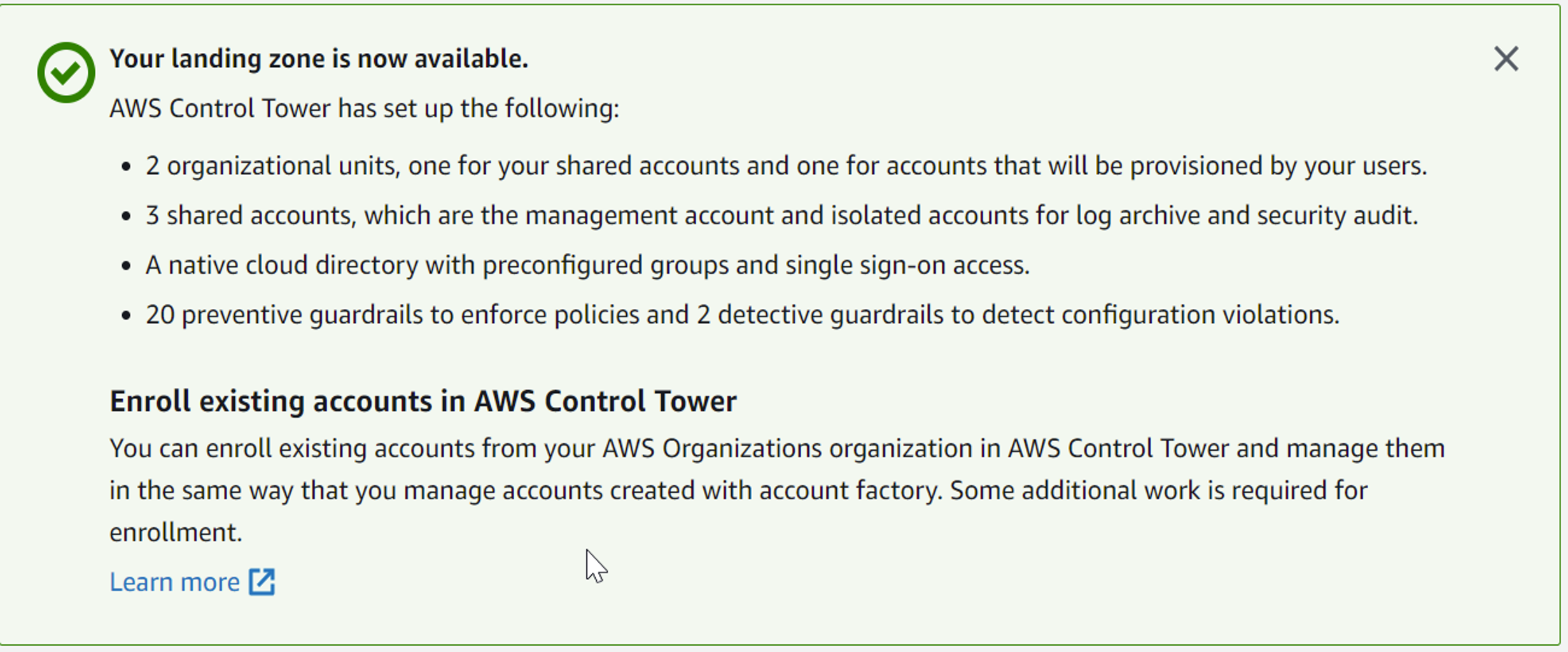
Screenshot of a successful AWS Control Tower deployment on 30th March 2022.
Guardrails enable governance
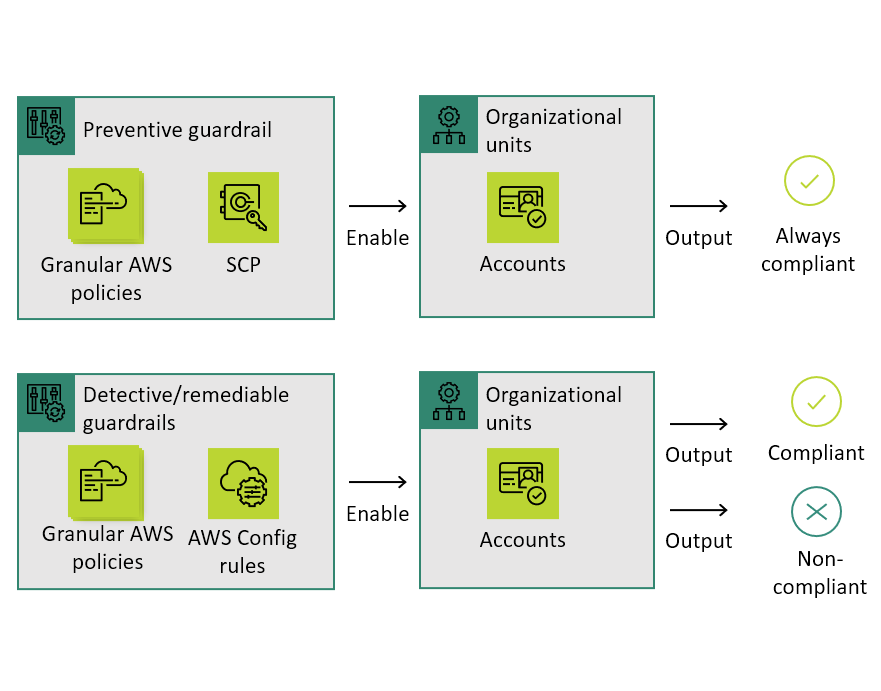
AWS Control Tower automatically implements guardrails using multiple building blocks such as AWS CloudFormation to establish a baseline, AWS Organizations service control policies (SCPs) to prevent configuration changes, and AWS Config rules to continuously detect non-conformance.
- Guardrails are preconfigured governance rules for security, compliance, and operations.
- Guardrails are expressed in plain English to provide an abstraction over granular AWS policies.
- Preventive guardrails: prevent policy violations through enforcement; implemented using AWS CloudFormation and Service Control Policies (SCPs).
- Detective guardrails: detect policy violations and alert in the dashboard; implemented using AWS Config rules.
- Mandatory and strongly recommended guardrails for prescriptive guidance.
- Easy selection and enablement on organizational units.
Centralized Identity and Access Management using AWS Single Sign-On
In AWS Control Tower, AWS Single Sign-On allows central cloud administrators and end-users to manage access to multiple AWS accounts and business applications. AWS Control Tower uses the AWS SSO service to set up and manage access to the accounts created through AWS Service Catalog.
AWS SSO offers a user portal where your users can find all their assigned AWS accounts, business applications, and custom applications in one place.
You can use AWS Single Sign-On (AWS SSO) to authenticate identities from external identity providers (IdPs) through the Security Assertion Markup Language (SAML) 2.0 standard. This enables your users to sign in to the AWS SSO user portal with their corporate credentials. For example, you can connect an external IdP such as Okta or Azure Active Directory (AD), to AWS SSO.
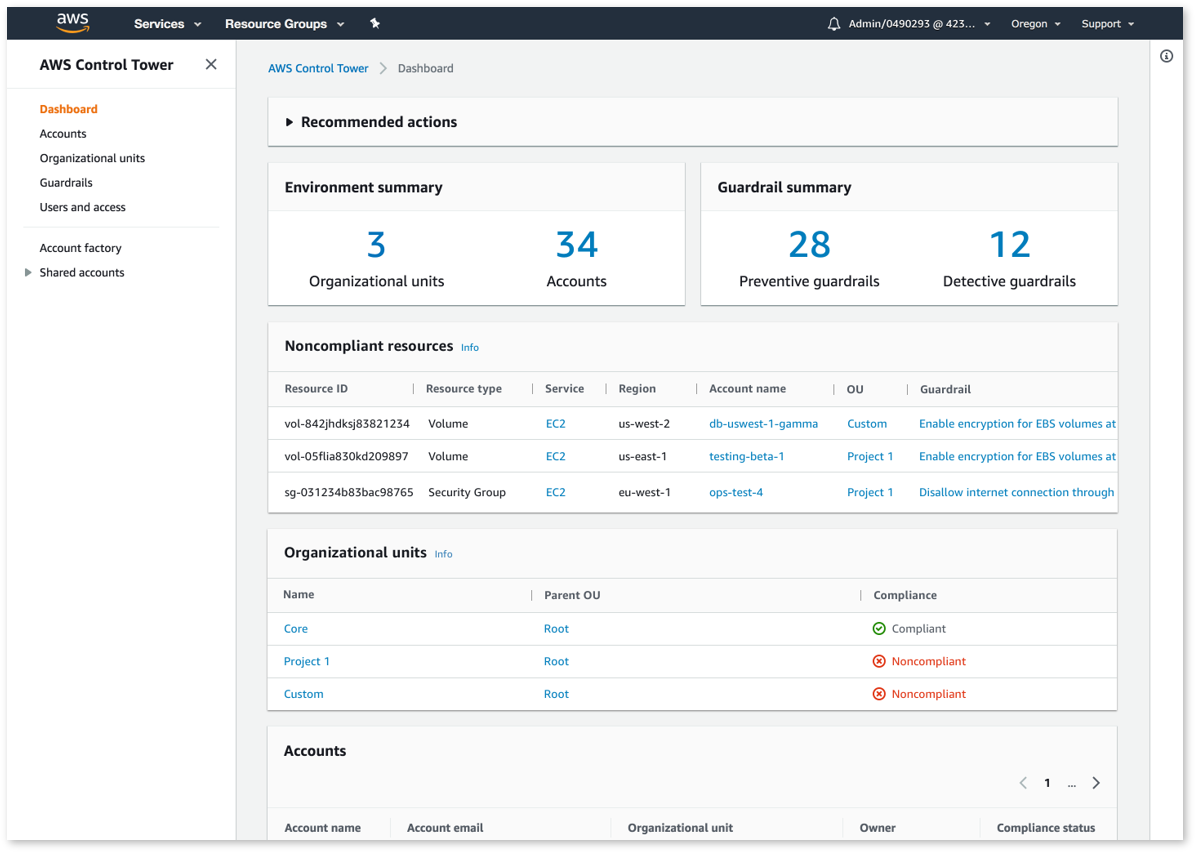
Dashboard for Visibility
AWS Control Tower offers a dashboard for continuous oversight of your multi-account environment. You get visibility into provisioned accounts across your organization. Dashboards provide reports on detective and preventive guardrails you have enabled on your accounts, and they give you the status of resources that don’t comply with policies you have enabled through guardrails.
Customizations for AWS Control Tower
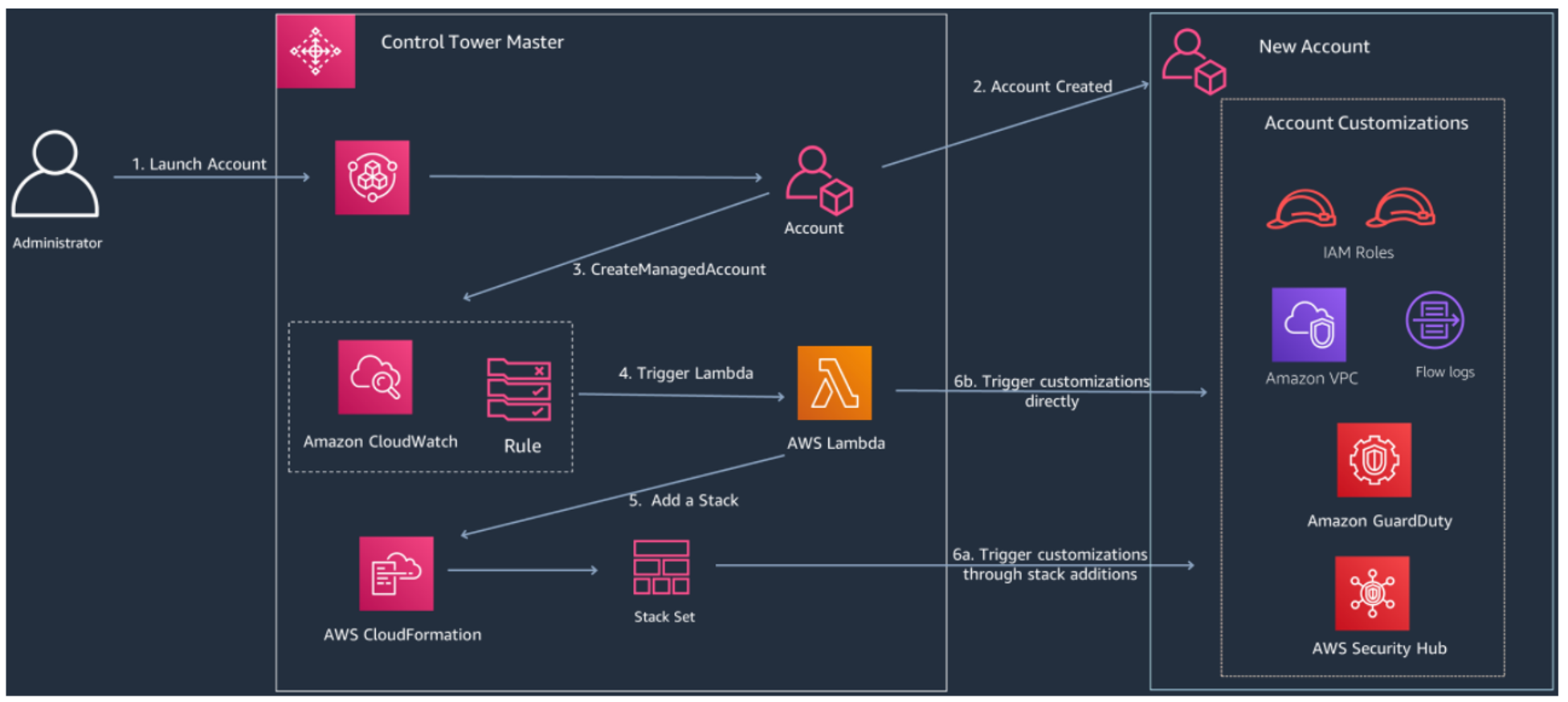
You can easily add customizations to your AWS Control Tower landing zone using an AWS CloudFormation template and service control policies (SCPs). You can deploy the custom template and policies to individual accounts and organizational units (OUs) within your organization. It also integrates with AWS Control Tower lifecycle events to ensure that resource deployments stay in sync with your landing zone. For example, when a new account is created using the AWS Control Tower account factory, Customizations for AWS Control Tower ensures that all resources attached to the account’s OUs will be automatically deployed.
- Control Tower records lifecycle events (CreateManagedAccount).
- Event Bridge can be used to trigger the instantiation of a Lambda or Pipeline for additional actions to be taken.
- Foundational services can be launched in each child account, or portfolio of self-service templates can be made available via AWS Service Catalog.
Summary
Control Tower is a solid tool to help you automate your multi account setup and security. It offers automation, simplified management, and multi-account governance that makes it easier to ensure you keep up with best practices across all of your accounts. You might consider using it if you are managing multiple accounts, build customization pipelines for enhancing the solution or simply wish to reduce your administrative overhead.